Recently a friend of mine inquired about my opinion on a Sonos (audio) device that was on their network that had been end of life for years. We were deliberating on what the threat landscape was for seemingly harmless devices like this on their network. That’s when I got curious and started doing some searching of my own.
THE TARGETS AND TECH
After some quick searching on Shodan I was able to find a slew of Sonos devices. They all interface on port 1400 and all deliver an “Error 403 — Forbidden” error if you try and send a traditional HTTP request to that port.
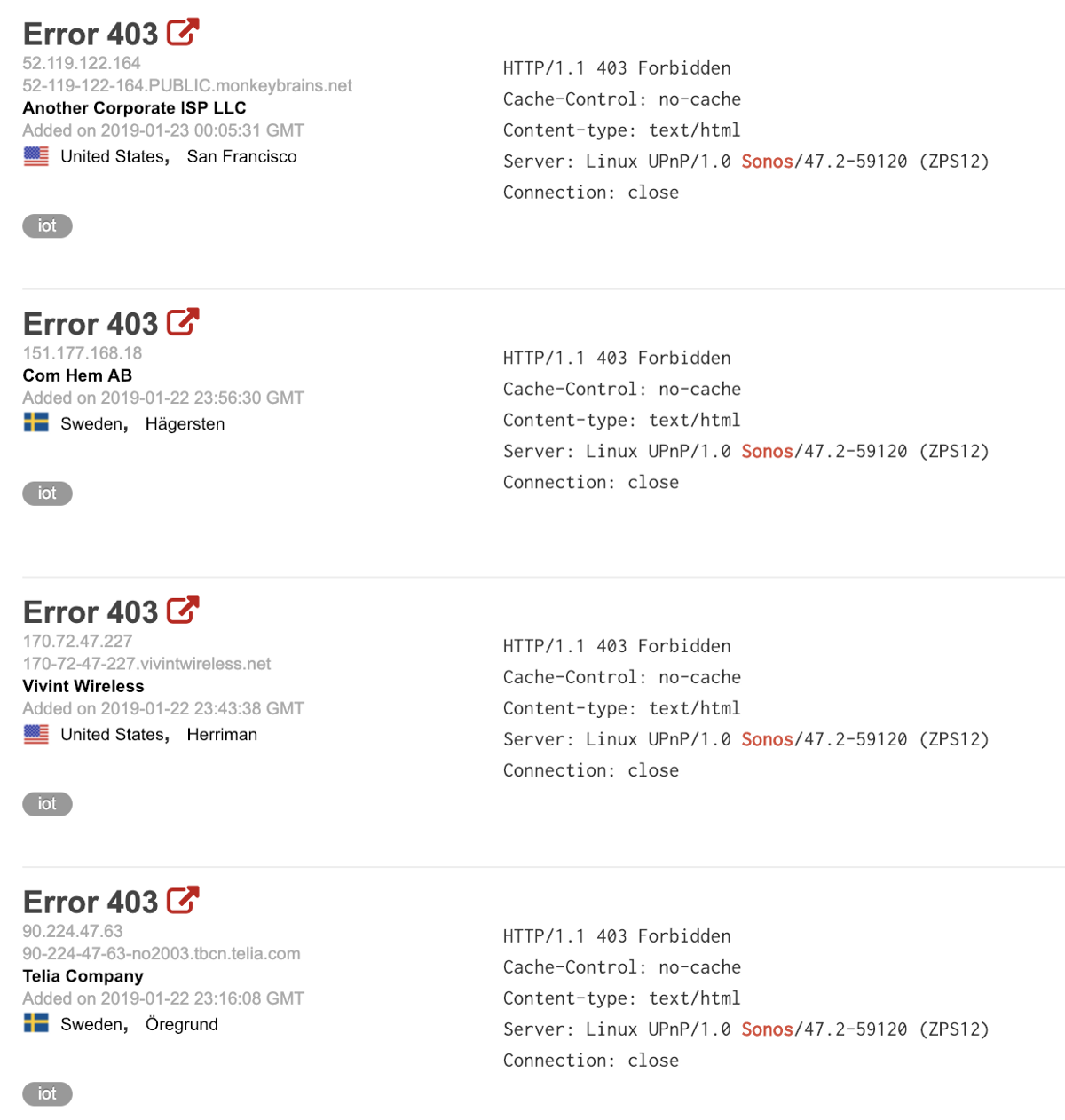
All devices seem locked out.
Enter “SoCo”. SoCo stands for Sonos Controller, a python project that was developed a few years ago by someone named Stefan Kögl. The code he developed is rather straightforward and includes a basic web application, also powered by python. It was designed to control local speakers on your network, but if I have an internet address to someone else’s, why not give it a shot?
IT WORKS
I picked one of the addresses at random, entered it into the python configuration file, and started the web server locally on my machine to see if it will let me control the device. No credentials, no keys, no anything. Just the address to the device. I opened my web browser, connected to my local web server that was running and voila, the speaker I picked was actually already playing something and I could not only see what it was but I could control it as well.
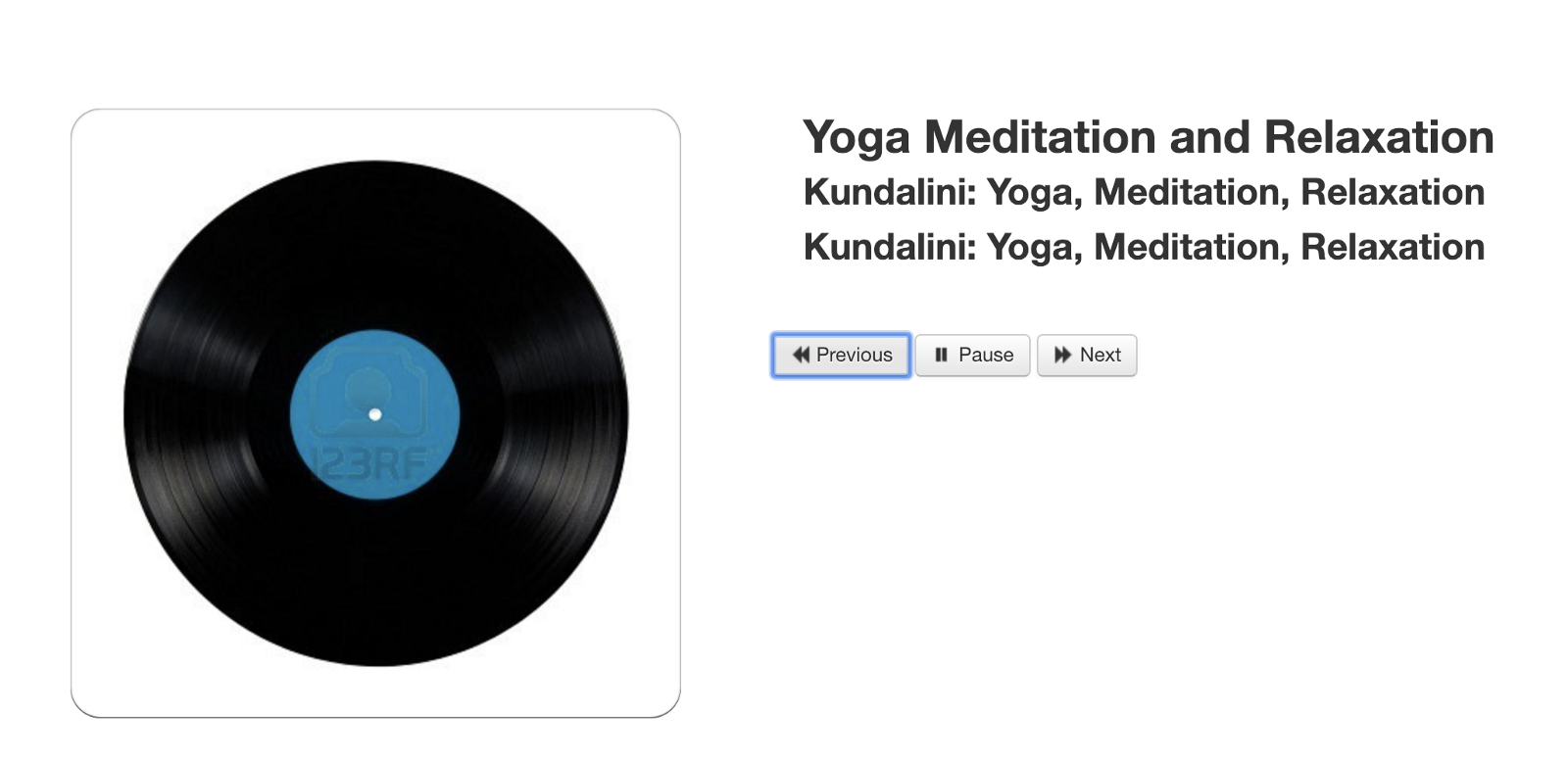
NOT SO SMART DEVICES
It turns out that a researcher at Trend Micro named Stephen Hilt also published a longer and more in depth report on the same issue. There’s obviously a design flaw here but you should certainly be aware that if you have any device in your home and it can connect to the internet, it’s not farfetched to assume it just may be sharing more with the internet than you think it is.