The Internet of Sonos
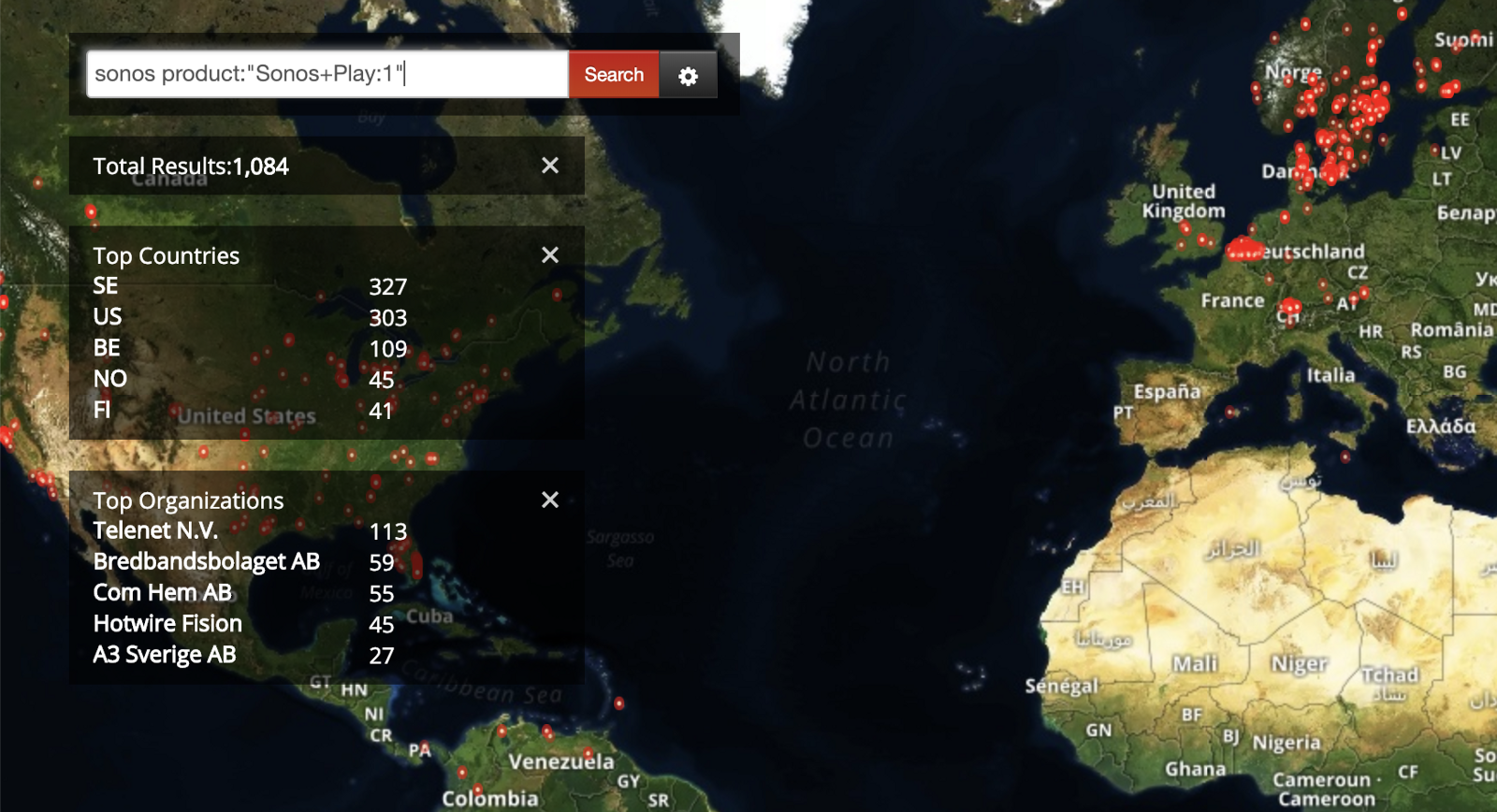
Recently a friend of mine inquired about my opinion on a Sonos (audio) device that was on their network that had been end of life for years. We were deliberating on what the threat landscape was for seemingly harmless devices like this on their network. That’s when I got curious...
[Read More]